How to protect your virtual privacy
Technology provides us secondary address which identifies us in the virtual world. It is as significant as our house address. In the era of information, data is the most crucial asset in the world. It not only plays a vital role in determining our identity but is also a decisive factor for real-world assets and identification. Hence it is more important to preserve our virtual identity. Although the virtual world has no shape and size and even not any physical existence, even then we use this address and associate with stuff more frequently than our physical address and identity. Whether we have to shop, communicate or transfer valuable assets or information, we always depend on our virtual identity because of its compatibility, easy access and universal presence.
Comfort comes with some caution and criticality. A small mistake can cause serious identity snooping. The privacy breach is the most serious cyber threat in front of whole cyber world. Association of real-world identity with virtual specification makes it more complex as well as important. Now, anyone can steal others money from its account without even knowing his real-world location with a single click. So it is very crucial to solidify and strengthen privacy.
Which activities can cause a privacy risk?
- Pharming: Pharming is the tool that diverts the information targeted to a particular domain to another domain. The primary intention is to get the information by creating an illusion. The steal of confidential data, bank account detail is the frequent target of this tool.
- Spyware: Evil software that intrudes into the targeted system, operates offline, gathers information and sends it to its source whenever the victim system gets the online connection without victims concern.
- Malware: A bad intended malicious set of instruction which contains virus, Trojans to spoil the information of the targeted system.
Ways to protect digital privacy
Here are some easy tips which help you to safeguard your privacy and identify any breach or breaching attempt.
- Use of preventive software: Use of anti-virus, anti-malware, anti-spam and firewalls limit the effectiveness of the security breach.
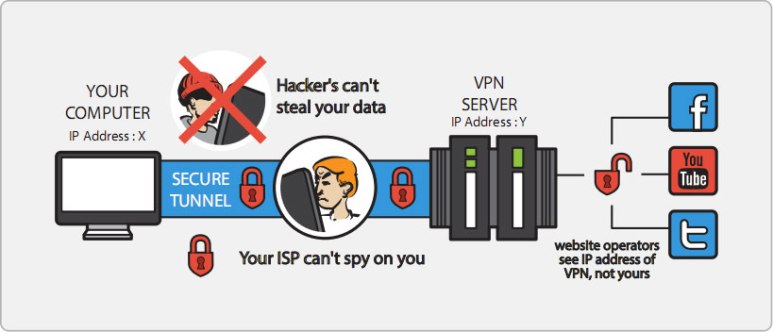
- Keep an eye on the internet service provider: ISP almost everything about your online activity. They can store your web browsers history and even save your text and message. So it is useful to get a VPN association with your browser to avoid such kind of snooping.
- Strengthen log in credentials: A strong password it the only tool that can safeguard your account from any security breach. So make is more critical and bulky. Use a different kind of alphabets, digits and special characters to make it unpredictable.
- Wi-Fi verification: Keep a deep eye on your Wi-Fi connection and its association with different devices. Change the password after some time. Wi-Fi could be the middle man in your security breach.
- Update your safeguarding tools: Update your antivirus, anti-malware, anti-spam time to time, so that they boosted with an additional feature which will help them to fight against cybercrimes.
- Avoid the exposure of your confidential information. Use your data with caution on a social media platform.
- Erase browser history, cookies and cache memory after some time.
- Use encrypted mode of communication on public platform. Enable encryption on Facebook and other social media sites.
Steve Rogers is a Microsoft Office expert and has been working in the technical industry since 2002. As a technical expert, Steve Rogers has written technical blogs, manuals, white papers, and reviews for many websites such as office.com/setup
Source : Office.com/setup


Comments
Post a Comment